Kubernetes Dashboard 安装及配置
基础准备
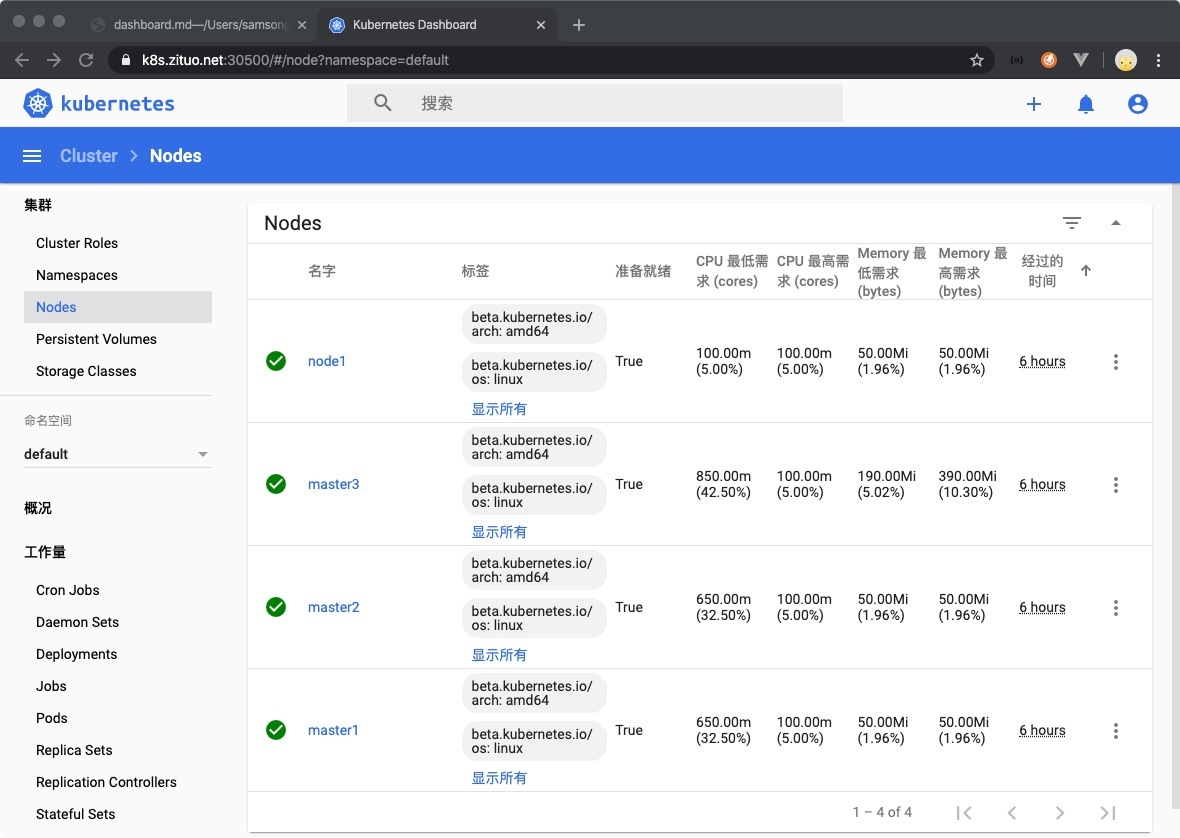
已经搭建好的k8s集群
$ kubectl get nodes
NAME STATUS ROLES AGE VERSION
master1 Ready master 5h31m v1.17.2
master2 Ready master 5h30m v1.17.2
master3 Ready master 5h29m v1.17.2
node1 Ready <none> 5h29m v1.17.2
完成后的界面

1.0 创建kubernetes-dashboard-certs
$ mkdir dashboard # 创建目录
$ cd dashboard
$ vi zituo.crt # 线上的ssl证书,复制进来
$ vi zituo.key # 线上的key,复制进来
$ kubectl create namespace kubernetes-dashboard # 创建一个namespace,因为kubernetes-dashboard还不存在
# 创建一个名为kubernetes-dashboard-certs的secert
$ kubectl create secret generic kubernetes-dashboard-certs \
--from-file=dashboard.crt=zituo.crt \
--from-file=dashboard.key=zituo.key \
-n kubernetes-dashboard
特别说明:如果通过
kubectl delete -f dashboard.yaml删除后,上述secret也会被删除
2.0 安装dashboard
官方文档
$ kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-rc5/aio/deploy/recommended.yaml
# 因为要跑自己的证书去掉了
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kubernetes-dashboard
type: Opaque
修改后的文档
$ vi dashboard.yaml
apiVersion: v1
kind: Namespace
metadata:
name: kubernetes-dashboard
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
type: NodePort # 此处为我添加,可直接通过30000以上的端口进行访问
ports:
- port: 443
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-csrf
namespace: kubernetes-dashboard
type: Opaque
data:
csrf: ""
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-key-holder
namespace: kubernetes-dashboard
type: Opaque
---
kind: ConfigMap
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-settings
namespace: kubernetes-dashboard
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
rules:
# Allow Dashboard to get, update and delete Dashboard exclusive secrets.
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"]
verbs: ["get", "update", "delete"]
# Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
# Allow Dashboard to get metrics.
- apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster", "dashboard-metrics-scraper"]
verbs: ["proxy"]
- apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"]
verbs: ["get"]
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
rules:
# Allow Metrics Scraper to get metrics from the Metrics server
- apiGroups: ["metrics.k8s.io"]
resources: ["pods", "nodes"]
verbs: ["get", "list", "watch"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
containers:
- name: kubernetes-dashboard
image: kubernetesui/dashboard:v2.0.0-rc5
imagePullPolicy: Always
ports:
- containerPort: 8443
protocol: TCP
args:
- --auto-generate-certificates
- --namespace=kubernetes-dashboard
# Uncomment the following line to manually specify Kubernetes API server Host
# If not specified, Dashboard will attempt to auto discover the API server and connect
# to it. Uncomment only if the default does not work.
# - --apiserver-host=http://my-address:port
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
# Create on-disk volume to store exec logs
- mountPath: /tmp
name: tmp-volume
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard
nodeSelector:
"beta.kubernetes.io/os": linux
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kubernetes-dashboard
spec:
ports:
- port: 8000
targetPort: 8000
selector:
k8s-app: dashboard-metrics-scraper
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kubernetes-dashboard
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: dashboard-metrics-scraper
template:
metadata:
labels:
k8s-app: dashboard-metrics-scraper
annotations:
seccomp.security.alpha.kubernetes.io/pod: 'runtime/default'
spec:
containers:
- name: dashboard-metrics-scraper
image: kubernetesui/metrics-scraper:v1.0.3
ports:
- containerPort: 8000
protocol: TCP
livenessProbe:
httpGet:
scheme: HTTP
path: /
port: 8000
initialDelaySeconds: 30
timeoutSeconds: 30
volumeMounts:
- mountPath: /tmp
name: tmp-volume
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
serviceAccountName: kubernetes-dashboard
nodeSelector:
"beta.kubernetes.io/os": linux
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
volumes:
- name: tmp-volume
emptyDir: {}
$ kubectl apply -f dashboard.yaml # 安装dashboard
成功后,发现kubernetes-dashboard的service跑在30500端口
$ kubectl get svc --all-namespaces
NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
default demo-app-service NodePort 10.97.84.23 <none> 10001:32051/TCP 5h2m
default kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 5h56m
kube-system kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 5h56m
kubernetes-dashboard dashboard-metrics-scraper ClusterIP 10.102.30.66 <none> 8000/TCP 51m
kubernetes-dashboard kubernetes-dashboard NodePort 10.105.199.184 <none> 443:30500/TCP 51m
$ sudo vi /etc/hosts
192.168.0.85 k8s.zituo.net
即可你使用 https://k8s.zituo.net:30500 访问dashboard界面。
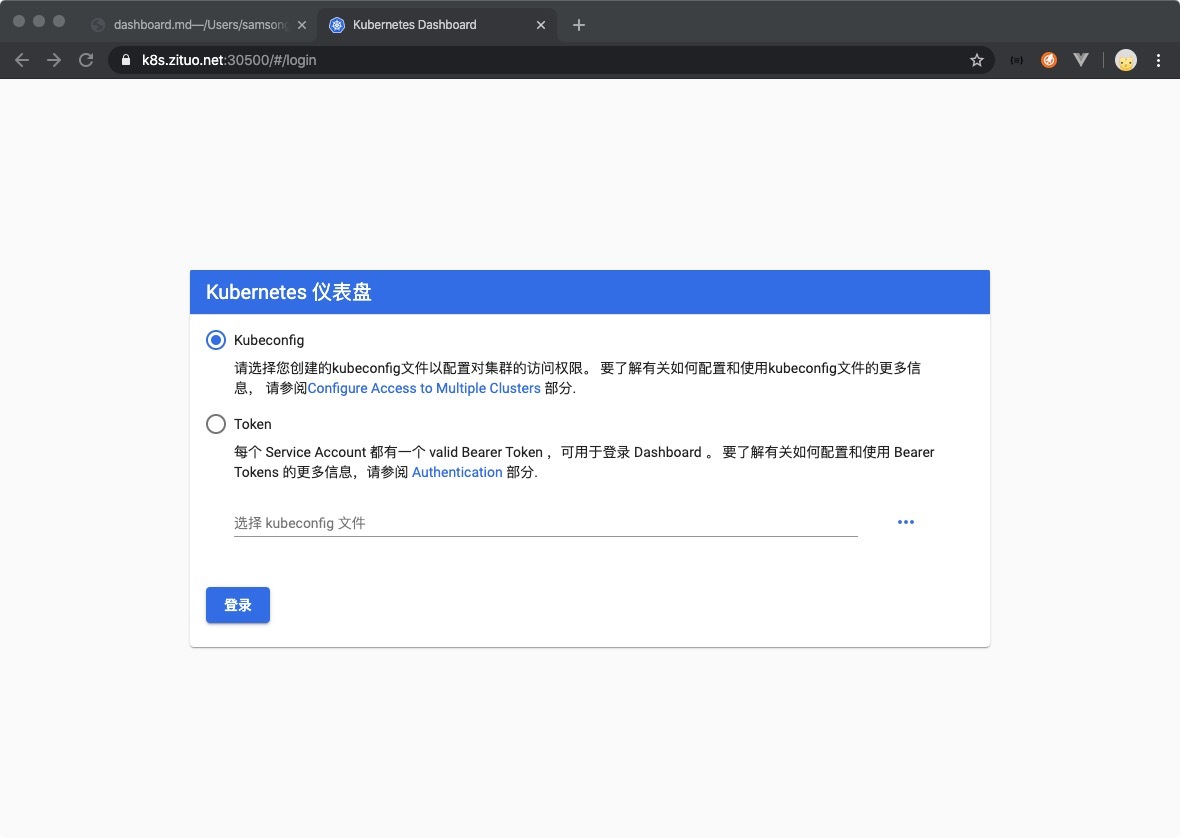
3.0 登录dashboard
3.1 创建登录用户
$ vi admin-user.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kube-system
$ kubectl apply -f admin-user.yaml
3.2 获取用户token
$ kubectl -n kube-system describe secret $(kubectl -n kube-system get secret | grep admin-user | awk '{print $1}')
Name: admin-user-token-rjtw2
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: admin-user
kubernetes.io/service-account.uid: 62e7c80a-4edc-45ae-bc84-82dc1a3b5d70
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6Ik9aT25IeHcwb0t6ZEtmUFhnY1hIdXBnRllyc2dDSHNVd1RUXzk0Um0yMVkifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi11c2VyLXRva2VuLXJqdHcyIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImFkbWluLXVzZXIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI2MmU3YzgwYS00ZWRjLTQ1YWUtYmM4NC04MmRjMWEzYjVkNzAiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZS1zeXN0ZW06YWRtaW4tdXNlciJ9.M8_ia4Rqb2wuaq4cTyOtgHxBP-pa0PNs9G-fJvwtUKEJ4bXmiJ8xXxfSFj5hdCJBmCQQhmkjSpWlYaafYyq3ruCuyRZ8g9eQrRQ70cKFJjOhR9tixuVOf3EWEnoi3JVxuZG4mcgfBMe8acLVDKF9YIOrmkgthOF2t1iApjxDWljpVj8KfN0WYVJXhk7iXWnDas3AQNLEmAZq7P_7Az9JQLpPw3w7P9zWuBtFZYgpYyMRY96s17NeEm3Xm6or6YVm40HXoT1PXHeumFbj82PfWV4XmVRIzJblXMdhz24eOez96M5gYCk6I6_kEcR67pCCMBRXstXM5mb26GrK0s7Wlg
3.3 使用token登录
复制3.2中token:后的内容完成登录
3.4 使用kubeconfig登录
复制服务器上的.kube/config到本地电脑
$ cd ~
$ mkdir .kube
$ vi config # 复制服务器上的.kube/config到本此,并添加token项
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUN5RENDQWJDZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJd01ESXhOakF5TlRreE9Wb1hEVE13TURJeE16QXlOVGt4T1Zvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTWpxCkFXWjNDeDZsUlB4dCtacFkrcGp5ZVVtZnNzaWtwT1UxeEFacmRxY1JnRUdKMFp6bktGQmMxTUhYSzdWNWh5aUsKV1VmU3NXdVN6NG9WTlFwLzU4dE9HQVNSY0RJTU9MMWhkemMxbXRyVU5TNzJJazY4R2ptR0MyczdxZkJYZEhXcgorOE0rVUkwTmlEblJGN1diLzJuQUlIZmgvVldtelUxS1FxbmxPdWwzMFdhUmZPSGtlODViZmIxWVhBWFdkVzRTCkxma3BuSWZEODVpcmM5Q3R3c09TNENVTFdIck8xNXNQbFlMa3haTlROZmFFZUEwaEltUEh5c2E1S0lvNUdJSGYKSk9tUzFNay9RRXJ0NHlYTDFEMlVEZ0Q0eTBwbmEzcnpRaDYzaW1xb3llcEl3SjFiTzNSc2hrZDBPK0dVOU1TbQprR29HZmFMeGJUbWZKUmxVZ09jQ0F3RUFBYU1qTUNFd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFBZ1NYVkVNSGd2ekk3V0cvd0FQdURVY2p3a0sKdXFNeVdhMm1TRzN4TXRhTFhGeTZ3Z3B0TzIyMVpPMCtEckdUWEpKMzl5REN2ZWc4UWVnNWd0d2hVS3JZZnB0cQpyZ0FYM3FnckNUUlp6VDBGaitYSkRLSEQ3TEFHZEo0WmozdkJDQlQ1cDZ0YnF2YXZPdnNKVTd4NENlRzFDQ0dyCkVwbktKb0lKS1lLYkxQMnc5TzdRMVFPVnd2dkhSMW5QTXFzNno2OThldFl3cUdPdUlQSkY3UW81TDBBRzhPT3EKcVhQWGFYa0RxV2VXa3NkWG8wcVBDOXZCMTR3azZyVHZjR01JY3IwVzdWYUUzZUVoSVRyeTBiTzR3Z2MzWWFhSwoxbnVwMUVTK1dBdVVCV0xSOVVPdkdGcVBNQnNFaWVhQ1ViZkRDNkI4eHBMQ3h3czloeG95S21HcHpnYz0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
server: https://192.168.0.100:8443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6Ik9aT25IeHcwb0t6ZEtmUFhnY1hIdXBnRllyc2dDSHNVd1RUXzk0Um0yMVkifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi11c2VyLXRva2VuLXJqdHcyIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImFkbWluLXVzZXIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI2MmU3YzgwYS00ZWRjLTQ1YWUtYmM4NC04MmRjMWEzYjVkNzAiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZS1zeXN0ZW06YWRtaW4tdXNlciJ9.M8_ia4Rqb2wuaq4cTyOtgHxBP-pa0PNs9G-fJvwtUKEJ4bXmiJ8xXxfSFj5hdCJBmCQQhmkjSpWlYaafYyq3ruCuyRZ8g9eQrRQ70cKFJjOhR9tixuVOf3EWEnoi3JVxuZG4mcgfBMe8acLVDKF9YIOrmkgthOF2t1iApjxDWljpVj8KfN0WYVJXhk7iXWnDas3AQNLEmAZq7P_7Az9JQLpPw3w7P9zWuBtFZYgpYyMRY96s17NeEm3Xm6or6YVm40HXoT1PXHeumFbj82PfWV4XmVRIzJblXMdhz24eOez96M5gYCk6I6_kEcR67pCCMBRXstXM5mb26GrK0s7Wlg
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM4akNDQWRxZ0F3SUJBZ0lJYnhSbmhDYkdRQkF3RFFZSktvWklodmNOQVFFTEJRQXdGVEVUTUJFR0ExVUUKQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TURBeU1UWXdNalU1TVRsYUZ3MHlNVEF5TVRVd01qVTVNakJhTURReApGekFWQmdOVkJBb1REbk41YzNSbGJUcHRZWE4wWlhKek1Sa3dGd1lEVlFRREV4QnJkV0psY201bGRHVnpMV0ZrCmJXbHVNSUlCSWpBTkJna3Foa2lHOXcwQkFRRUZBQU9DQVE4QU1JSUJDZ0tDQVFFQXhwbzJKRGhpRVdSWGNEcW4KOUhoNndTQ2c3SnRzeTRTeGF4OWFkdTczZUxsL2RQdTlJR3JyZ0YyandXQkFSS1JkaGJoYkJzc3ZkU2tWaGNJeQo3TUdwenBJMXdKcmE3MFpQZXptRFBXWHY0OWFpY2FWZmNxa2JmcjlLdEJKMUlSZm03b2J2MEdJSW5YNkxhOE10ClFOY20zU29Zb1g1Yk9KWEcxUm9BWm1Pa0M0Ukt2ak41QnVTd05DSU5aZWo2YTZtYzgrNDBKbXpHNEM5Zi95WEMKN3Vodk9WNVlrQjg5ejFKYklHL095d0o4cjFHWHF5MzNPbkc3T0hCVXBTZjFEeHhrK0VFcklPcXJ3Q1hPOGtlYQpyRVVHZ0YyM2RKN0NVNVJvZE9uN3dCRjJzbVFVK0gwN0xFcXpwT0I2N3k4eXI0bFEwdlkvd21JZ1lpa1RwbjJ6Ckljd3RQd0lEQVFBQm95Y3dKVEFPQmdOVkhROEJBZjhFQkFNQ0JhQXdFd1lEVlIwbEJBd3dDZ1lJS3dZQkJRVUgKQXdJd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFLTlBqdVkwYlp6ZXVQSXoxWDllRG1WVndlQkpkU3VZM29SMwpmeU1KN0VKWHZ6NlhIUkJ6TkxqRFdHS2tjQ2hCaFo0L2F3VUpyUjU0dDFlTGZPT3padEVmWHRmTWFHTkc5dDg2CkUraGlETzQ5eVhrZWwvVG9GM2tlaFZOSFZVOEZQTStkNXNLYmEySHMvanE5WHhua1k0VzVmZGRTMmxyckNtQkcKcitvS1FCaW5sazRsc1ZWVE5HYkRwdnQ2WlEvbFZIY3FOUHpqeHFrbnZ1QXNOYzF4T3hPcm9PbzN5NCtMNTVZYgo0RitwdGIxdURYeml0K1dJbGpKQklRZTZRamEwVUVvZllqTDd5QnNkTFdKUThWVTVtZk5pZHlkaEl4Mk8xbmhjCkFhWVEyQTgyakdIMGRjZDRzWURqSE13R1lQd3c4UjNRM3NkM295WUxreEttb0FQMnMwcz0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcEFJQkFBS0NBUUVBeHBvMkpEaGlFV1JYY0RxbjlIaDZ3U0NnN0p0c3k0U3hheDlhZHU3M2VMbC9kUHU5CklHcnJnRjJqd1dCQVJLUmRoYmhiQnNzdmRTa1ZoY0l5N01HcHpwSTF3SnJhNzBaUGV6bURQV1h2NDlhaWNhVmYKY3FrYmZyOUt0QkoxSVJmbTdvYnYwR0lJblg2TGE4TXRRTmNtM1NvWW9YNWJPSlhHMVJvQVptT2tDNFJLdmpONQpCdVN3TkNJTlplajZhNm1jOCs0MEptekc0QzlmL3lYQzd1aHZPVjVZa0I4OXoxSmJJRy9PeXdKOHIxR1hxeTMzCk9uRzdPSEJVcFNmMUR4eGsrRUVySU9xcndDWE84a2VhckVVR2dGMjNkSjdDVTVSb2RPbjd3QkYyc21RVStIMDcKTEVxenBPQjY3eTh5cjRsUTB2WS93bUlnWWlrVHBuMnpJY3d0UHdJREFRQUJBb0lCQUNOU2VoNm5DSW9mVm8zWApZTmZTTmNMemtxdUNXUzg1UW5UUzlyd0FkSE04U3JiN3J2OTlCTFduOGVBS3htTnUrRk00SHJodW10b3puR2hWCnljamlDTmw4bDZMUjUrNTJpdHhYdGtmTlFZVThQMWdIR1pyRENPamFET2RLQVJzSnJVRHZMdWZaQjc4N0tvRFkKRGN4aWQ3OE9KYU5UWGRZS2pYcUpUVmpvajl5Y01vRVltVlZGTndBWnQwWGNIMDBFanJpZE9HbUlndlRocWI3QgpKNW5VU3JXZkZTdjRKQnIrZVVOTWpzM2NKeXNIZk01YStnRUJSSjE3ZUppaGhVSGRRM1RiU2R4a3JqNnY3cExzClJGTm5VQXhQT2cwQUF3TExyNW9KeEVBRlR5NVdNLzhRTWVnTFRDWjJZL2xGWm5ldXdTTERqZjh5WDJ1ZkJoQnIKNExlcTNNRUNnWUVBN051dlhER0VucmhheCtNREh3SVBDUW00MnV3dlJXZmpSME5TeTZ4UWNOYVl1WkF4UzVPOQpLK2dlMXc3ZklZQVVmWXJZYUYrL1A2NW1paTkwM3VmN3kzajcyQ0lPR25pT25rQk9EK1BUZDM2VmcwY05QYS94Ci9reVRkZVFlekR6TFdsNHlnLzIzSjBONTRxL1pwSTlHNm9lYlZUZU8xY3l4SjgrRHQwK0ZneDBDZ1lFQTFxY1AKWkdSQkRQbGtBMGZKZEpuV2FScjNwM0ZrRDlqVkxPNHY4dnBMU1l0KzdVdmtkT01sc2VlS1lHYXVaeVo3cC9kbQphdXhmRTEvZUZUZ29Kc1UwZzAvYndTc3J3SGhNN1lPRzB3RWRyQmdjd05MY01SNU4yVUNPRlRHb0wyTUhpK3owCnhuYUFJUHlxdHRQR0F0dHgwbEdUMDlEc1JZaFRLWVljT0lsMHh3c0NnWUVBcjJ6cURWTlRrU2FqZmVZaDJxWncKc2xYMEJwamxUZmRxdXM0ZkZXQnpWNDlwSUE2dW8vWXhKc0xOaktTa0dEQy9mRmdJZmcxa0hXc3k0T2ZUSElFZQoyWTJxb1dKZnBiVmlrOHkyeEVnTnlEUUYwbXdlWDNEZnYyUEIxNC8wUzNvL2RwZkx2RHgrbVdMOWRDcWYvS1J0CmRxaW5JRTk4eDliSjR0MXNCYW10RGZVQ2dZQVViejBBNHFacXRNYzNwTHJoOWM4Nm5FMmRUQ2NwZHd2OFJnU2MKamdWaXovdmFYVkkzYW5ScE5sQ3ZFcmRocklFeklWTkh0STdzaWtEYkpraDBRR3ZhWUZ6Y1M5N1RhT0J4OEFhQwp5ZVZvUDdkbEIrM2NZelVvRElRNk1rci9qOTdsREQ3Vk1lekt0eU1OV3FYTUdkWUJIckVEQmkyb0JPMWQwNTJXCktFZk10d0tCZ1FDMnRvUDEwNVVkWW5LWjE4ZEZLdTQwZ2diVU9laW1JcjkzaEVwK2FNZVUrWjBIOEpkOHdUZisKSU1paGQ5MFFzM3ZlaFpFMEhkT1U2MXg3cnozUXVVSzZWczVYQjhrOXYyTzlOKy9IWDErZ3BEcWxqcFY2am5OeQpjRnZRVUpBdm9iVGhVL0pzOWFZS3V2bTVWNU1nYld0YjZ6NU8xSFN3RDAydk9JT1hyRUcybHc9PQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=
登录时上传本地config文件完成登录